The Relationship Between Tor Routing and Bitcoin
After extensive research on Bitcoin, ironically, my first blog post isn’t about Bitcoin but about the Tor network (Tor Project)1. The Tor network is aptly named for its method of wrapping data packets in multiple layers, akin to the layers of an onion.

From what I understand, the Tor network has numerous relay stations around the world2. These volunteer-operated relays are responsible for transmitting the data packets we send. Before sending, however, the sender needs to know which relays are available. This information is likely stored on a server, including each relay’s public key generated by RSA (which has been deemed insecure in version 3 of Tor and replaced with ECC). The private key, naturally, belongs to the relay itself for decrypting the data.
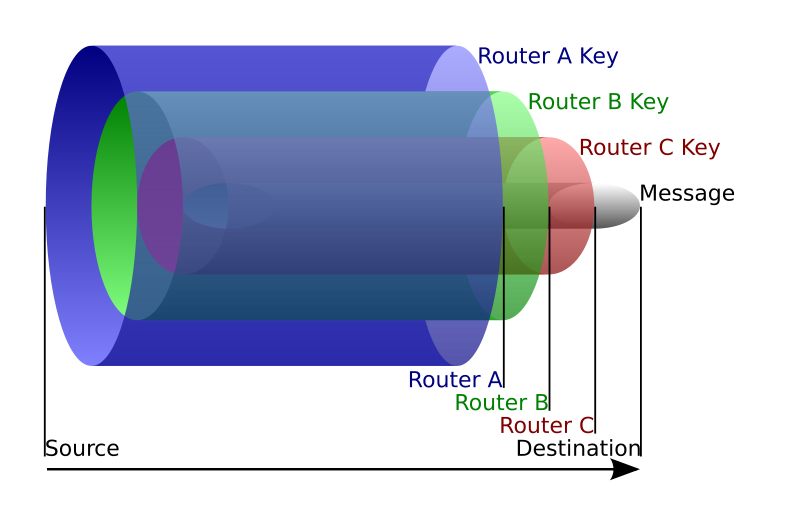
The next step involves requesting data from this server. Let’s say we request information on a hundred relays and randomly select ten. We then encrypt our data packet with each selected relay’s public key, layer by layer. Once the packet is fully encrypted, it’s sent through the Tor network. The outermost relay, which has the corresponding public key, receives and decrypts one layer, revealing the next relay’s public key, and so on, until the packet reaches its exit node. It’s important to note that each relay only knows its immediate predecessor and successor, making it incredibly difficult to trace the full path of the data.
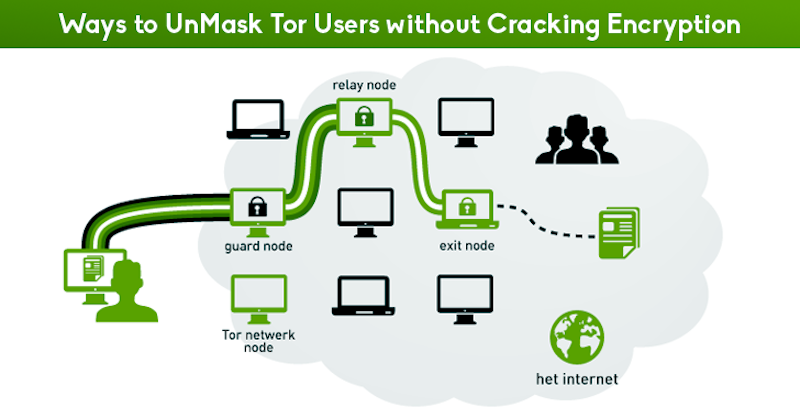
In addition to explaining the packet transmission process within the Tor network, it’s worth discussing its vulnerabilities, particularly at the entry and exit points. The entry point, for an Internet Service Provider (ISP), marks the initiation of a Tor session. The exit point might be, for example, a packet headed to Facebook from the Tor network. This resembles Bitcoin’s money laundering process. Furthermore, packets at the entry point are usually encrypted with RSA public keys, while at the exit point, they’re mostly decrypted, often leaving only HTTPS encryption if the initial protocol was HTTP.
A common tool used to access the Tor network is the Tor Browser, a combination of Firefox and Tor. This browser can interpret .onion domains, which are not conventional IP addresses but paths to the destination. The Tor Browser can operate as a standalone Tor program, employing a local SOCKS5 proxy at 127.0.0.1:9050, essentially creating a local entry point to the Tor network. Since traditional browsers and apps use standard DNS resolution, the lack of .onion domain resolution isn’t unusual.
Conclusion: Tor routing makes it more difficult for ISPs to track users, a feature beneficial for Bitcoin transactions to prevent ISPs or hackers from seeing the transaction’s origin. Although Bitcoin addresses might indicate the transaction initiator, the lack of encryption during Bitcoin’s data transmission makes it vulnerable to tampering. However, there have been proposals for HTTPS-based blockchain synchronization mechanisms in Bitcoin Improvement Proposals (BIP)3. The current Bitcoin Core 4 also supports Tor network options.
- #4587 0c465f5: Allow users to set -onion via GUI (Diapolo)
References
Enjoy Reading This Article?
Here are some more articles you might like to read next: